(Press-News.org) Edward Snowden's leak of classified documents to journalists around the world about massive government surveillance programs and threats to personal privacy ultimately resulted in a Pulitzer Prize for public service.
Though Snowden had no intention of hiding his identity, the disclosures also raised new questions about how effectively news organizations can protect anonymous sources and sensitive information in an era of constant data collection and tracking.
A new study by University of Washington and Columbia University researchers that will be presented next month at the 24th USENIX Security Symposium probed the computer security habits of 15 journalists across two continents and found a number of security weaknesses in their technological tools and ad-hoc workarounds.
Those included computer security tools that go unused because they introduce roadblocks to information gathering, inadequate solutions for basic tasks like transcribing interviews and failing to consider potential risks from cloud computing and other common practices.
"The way people try to bridge gaps can introduce security issues," said UW senior author Franziska Roesner, an assistant professor of computer science and engineering who focuses on computer security and privacy.
"If you use your iPhone to translate speech to text, for example, it sends that information to Apple. So if you record a sensitive conversation, you have to trust that Apple isn't colluding with an adversary or that Apple's security is good enough that your information is never going to be compromised."
News organizations' abilities to build trust with sources and gather sensitive information have been called into question by recent disclosures about surveillance: the U.S. Department of Justice's admission that it secretly obtained phone records from the Associated Press, Microsoft's admission that it read a blogger's personal Hotmail account to find a source of an internal leak and criminal investigations that have used email traces to identify and prosecute anonymous sources.
"Addressing many of the security issues journalists face will require new technical solutions, while many existing secure tools are incompatible with the journalistic process in one way or another," said lead author Susan McGregor, assistant professor at Columbia Journalism School and assistant director of the Tow Center for Digital Journalism.
"At the same time, there are clearly opportunities to build tools that really support journalists' workflow and build them in a secure way."
The researchers interviewed 15 working journalists from the U.S. and France about how they communicate with sources, what strategies they use to organize notes and protect sensitive information, and their use of existing information security tools. They found some reporters took steps to lessen certain types of security risks, but not others.
One journalist who went to great pains to protect the identity of sources by only meeting in person, for instance, used an iPad to photograph sensitive documents. Although roughly one-third of the reporters used encryption services to communicate with sources or protect their notes, a majority also used popular cloud services like Google Drive or Dropbox to store and share information.
That may be fine for the average user -- or even most journalists -- but anyone working with sensitive material ought to consider how much they trust that those servers will never be hacked, Roesner said.
"The flip side is that it's not just a matter of giving journalists information about the right tools to use -- it's that the tools are often not usable," Roesner said. "They often fail because they're not designed for journalists."
For instance, the team found that reporters' number one goal -- obtaining information -- was often impeded by existing security tools that introduce roadblocks to communication. The communication methods that reporters used were driven by the preferences of sources, who have widely different experiences with and access to technology.
One open-source product that sought to let whistleblowers securely send documents to journalists was rarely used because it lacked the common mechanisms by which news organizations tend to authenticate a source's identity. Encryption tools that garble the content of an email or message unless someone knows the secure key can still leave behind traces of "metadata," which leak investigations or criminal prosecutions can use to prove a relationship between a reporter and a source existed.
One of the study's goals was to identify opportunities for the computer security community to better serve journalists, Roesner said. That might include building security applications into a wider content management tool that accomplishes other tasks that reporters would find helpful, such as transcribing interviews and tagging or organizing notes.
"Tools fail when the technical community has built the wrong thing," said Roesner. "We've been missing a deeper understanding of how journalists work and what kinds of security tools will and won't work for them."
INFORMATION:
The research was partially funded by the National Science Foundation's Division of Computer and Network Systems. Co-authors include Polina Charters and Tobin Holliday, students in the UW Master of Human Computer Interaction and Design program.
For more information, contact Roesner at franzi@cs.washington.edu and McGregor at sem2196@columbia.edu.
Amsterdam, The Netherlands, July 22, 2015 - In a large population-based study of randomly selected participants in Germany, researchers found that mild cognitive impairment (MCI) occurred significantly more often in individuals diagnosed with a lower ankle brachial index (ABI), which is a marker of generalized atherosclerosis and thus cumulative exposure to cardiovascular risk factors during lifetime. Interestingly, this strong association was only observed in patients with non-amnestic MCI, but not amnestic MCI. There also was no independent association of MCI and intima ...
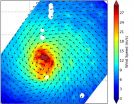
Typhoon Halola's strongest typhoon-force winds were located on the northern half of the storm, as identified from the RapidScat instrument that flies aboard the International Space Station.
RapidScat gathered surface wind data on the Typhoon Halola on July 21at 2 p.m. GMT (10 a.m. EDT). RapidScat data showed that the strongest sustained winds stretched from northwest to northeast of the center at speeds up to 30 meters per second (108 kph/67 mph). Strong winds wrapped around the center of circulation from northwest to east to the southern quadrant, while the weakest winds ...
Much to his own surprise, Hannes Baur from the Natural History Museum Bern not only reports on whole two new parasitoid wasps at the heart of Europe, the Swiss Alps and Swiss Central Plateau. While the common discovery usually involves cryptic, or "camouflaging" within their groups species, his stand out. Baur's work is published in the open-access journal ZooKeys.
The insects he describes are visibly quite unique with their body structures. In the case of the Pteromalus briani wasp, its extraordinarily protruding hind legs differentiate it among the whole family. Meanwhile, ...
CHAMPAIGN, Ill. -- A study of the West Nile virus risk associated with "dry" water-detention basins in Central Illinois took an unexpected turn when land managers started mowing the basins. The mowing of wetland plants in basins that failed to drain properly led to a boom in populations of Culex pipiens mosquitoes, which can carry and transmit the deadly virus, researchers report.
A paper describing their findings is in press in the journal Ecological Applications.
The team, led by University of Illinois postdoctoral researcher Andrew Mackay, found that mowing down cattails ...
GeoSpace
Warmer air, less sea ice lead to mercury decline in Arctic Ocean
The amount of mercury in the Arctic Ocean is declining as the region rapidly warms and loses sea ice, according to a new study. A new study in Geophysical Research Letters suggests that fish, marine mammals, polar bears, whales and humans in the Arctic might potentially be consuming lower amounts of toxic methylmercury as the region warms.
Eos.org
Puzzles invite you to explore Earth with interactive imagery
The EarthQuiz challenge can take you to virtual field locations with just the click of ...
The Mississippi River delta is a rich ecosystem of barrier islands, estuaries, and wetlands that's home to a diverse mix of wildlife -- as well as more than 2 million people. Over the past few decades, the shape of the delta has changed significantly, as ocean waves have carved away at the coastline, submerging and shrinking habitats.
To keep flooding at bay, engineers have erected dams and levees along the river. However, it's unclear how such protective measures will affect the shape of the river delta, and its communities, over time.
Now researchers from MIT and ...
MELBOURNE, FLA. -- The coral reefs that have protected Pacific Islanders from storm waves for thousands of years could grow rapidly enough to keep up with escalating sea levels if ocean temperatures do not rise too quickly, according to a new study from Florida Institute of Technology.
The study, published Wednesday in the journal Royal Society Open Science, provides the first evidence that well-managed reefs will be able to keep up with sea-level rise through vertical growth. But that can happen only if carbon dioxide levels in the atmosphere stay below 670 parts-per ...
PITTSBURGH, July 22, 2015 - Late- and post-menopausal women have significantly greater volumes of fat around their hearts - a risk factor for heart disease - than their pre-menopausal counterparts, a University of Pittsburgh Graduate School of Public Health study has shown for the first time.
The finding, published online and scheduled for the Sept. 1 issue of The Journal of Clinical Endocrinology & Metabolism, likely can be attributed to changing hormone levels and could guide potentially life-saving interventions. The work was funded by the National Institutes of Health ...
Electronic cigarettes or "e-cigs" have been touted as a tool smokers can use to wean themselves off of traditional cigarettes, which many believe are more harmful than their "e" counterparts. But because e-cig liquid also contains nicotine and emits carcinogens, is that perception really true? One team now reports in the ACS journal Chemical Research in Toxicology that much of the nicotine in e-cigarettes is the addictive form of the compound.
Although e-cigs don't burn tobacco, they heat and vaporize a liquid that contains nicotine, flavorings and other substances. ...
Stem cells hold great potential for addressing a variety of conditions from spinal cord injuries to cancer, but they can be difficult to control. Scientists are now reporting in the journal ACS Nano a new way to mimic the body's natural approach to programming these cells. Using this method, they successfully directed adult stem cells to turn specifically into muscle, which could potentially help treat patients with muscular dystrophy.
In the 1990s, scientists first isolated human embryonic stem cells, which can turn into any kind of cell in the body, and the promise ...