(Press-News.org) Computer science researchers have developed a new way to identify security weaknesses that leave people vulnerable to account takeover attacks, where a hacker gains unauthorized access to online accounts.
Most mobiles are now home to a complex ecosystem of interconnected operating software and Apps, and as the connections between online services has increased, so have the possibilities for hackers to exploit the security weaknesses, often with disastrous consequences for their owner.
Dr Luca Arnaboldi, from the University of Birmingham’s School of Computer Science, explains: “The ruse of looking over someone’s shoulder to find out their PIN is well known. However, the end game for the attacker is to gain access to the Apps, which store a wealth of personal information and can provide access to accounts such as Amazon, Google, X, Apple Pay, and even bank accounts.”
To understand and prevent these attacks, researchers had to get into the mind of the hacker, who can build a complex attack by combining smaller tactical steps.
Dr Luca Arnaboldi worked with Professor David Aspinall from the University of Edinburgh, Dr Christina Kolb from the University of Twente, and Dr Sasa Radomirovic from the University of Surrey to define a way of cataloguing security vulnerabilities and modelling account takeover attacks, by reducing them their constituent building blocks.
Until now, security vulnerabilities have been studied using ‘account access graphs’, which shows the phone, the SIM card, the Apps, and the security features that limit each stage of access.
However, account access graphs do not model account takeovers, where an attacker disconnects a device, or an App, from the account ecosystem by, for instance, by taking out the SIM card and putting it into a second phone. As SMS messages will be visible on the second phone, the attacker can then use SMS-driven password recovery methods.
The researchers overcame this obstacle by developing a new way to model how account access changes as devices, SIM cards, or Apps are disconnected from the account ecosystem.
Their method, which is based on the formal logic used by mathematicians and philosophers, captures the choices faced by a hacker who has access to the mobile phone and the PIN.
The researchers expect this approach, which is published in the Proceedings of the 28th European Symposium on Research in Computer Security (ESORICS 23), to be adopted device manufacturers and App developers who wish to catalogue vulnerabilities, and further their understanding of complex hacking attacks.
The published account also details how the researchers tested their approach against claims made in a report by Wall Street Journal, which speculated that an attack strategy used to access data and bank accounts on an iPhone could be replicated on Android, even though no such attacks were reported.
Apps for Android are installed from the Play Store, and installation requires a Google account, and the researchers found that this connection provides some protection against attacks. Their work also suggested a security fix for iPhone.
Dr Arnaboldi said: “The results of our simulations showed the attack strategies used by iPhone hackers to access Apple Pay could not be used to access Android Pay on Android, due to security features on the Google account. The simulations also suggested a security fix for iPhone – requiring the use of a previous password as well as a pin, a simple choice that most users would welcome.”
Apple has now implemented a fix for this, providing a new layer of protection for iPhone users1.
The researchers repeated this exercise across other devices (Motorola G10 Android 11, Lenovo YT-X705F Android 10, Xiaomi Redmi Note Pro 10 Android 11, and Samsung Galaxy Tab S6 Lite Android). Here they found that the devices that had their own manufacturer accounts (Samsung and Xiaomi) had the same vulnerability as Apple – although the Google account remained safe, the bespoke accounts were compromised.
The researchers also used their method to test the security on their own mobile devices, with an unexpected result. One of them found that giving his wife access to a shared iCloud account had compromised his security – while his security measures were as secure as they could be, her chain of connections was not secure.
Dr Arnaboldi is currently engaged in Academic Consultancy where he works with major corporates and internet-based companies to improve their defences against hacking.
END
Researchers unveil new way to counter mobile phone ‘account takeover’ attacks
2024-01-22
ELSE PRESS RELEASES FROM THIS DATE:
What factors affect patients’ decisions regarding active surveillance for low-risk prostate cancer?
2024-01-22
Because low-risk prostate cancer is unlikely to spread or impact survival, experts and guidelines recommend active surveillance, which involves regular monitoring and thus avoid or delay treatment like surgery or radiation therapy and their life-changing complications. A new study examined the rates of active surveillance use and evaluated the factors associated with selecting this management strategy over surgery or radiation, with a focus on underserved Black patients who have been underrepresented in prior studies. The findings are published by Wiley online in CANCER, a peer-reviewed journal of the American Cancer Society.
For the study, called the Treatment ...
New sustainable method for creating organic semiconductors
2024-01-22
Researchers at Linköping University, Sweden, have developed a new, more environmentally friendly way to create conductive inks for use in organic electronics such as solar cells, artificial neurons, and soft sensors. The findings, published in the journal Nature Communications, pave the way for future sustainable technology.
Organic electronics are on the rise as a complement and, in some cases, a replacement to traditional silicon-based electronics. Thanks to simple manufacturing, high flexibility, and low weight combined with the electrical properties typically associated with traditional semiconductors, it can be useful for applications such as digital displays, energy storage, ...
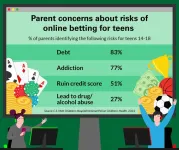
Digital dice and youth: 1 in 6 parents say they probably wouldn’t know if teens were betting online
2024-01-22
As young people increasingly have access and exposure to online gambling, only one in four parents say they have talked to their teen about some aspect of virtual betting, a national poll suggests.
But over half of parents aren’t aware of their state’s legal age for online gambling and one in six admit they probably wouldn’t know if their child was betting online, according to the University of Michigan Health C.S. Mott Children’s Hospital National Poll on Children’s Health.
“Teens and young adults may have a difficult time going ...
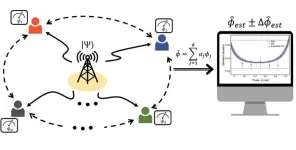
Enable distributed quantum sensors for simultaneous measurements in distant places
2024-01-22
We've all had the experience of trying to get the exact time of a highly competitive concert ticket or class beforehand. If the time in Seoul and Busan is off by even a fraction of an hour, one will be less successful than the other. Sharing the exact time between distant locations is becoming increasingly important in all areas of our lives, including finance, telecommunications, security, and other fields that require improved accuracy and precision in sending and receiving data.
The Korea Institute of Science and Technology (KIST) announced that Dr. Hyang-Tag Lim and his team at the Center ...
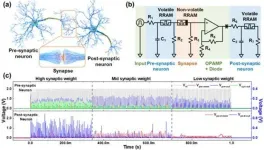
Implement artificial neural network hardware systems by stacking them like "neuron-synapse-neuron" structural blocks
2024-01-22
With the emergence of new industries such as artificial intelligence, the Internet of Things, and machine learning, the world's leading companies are focusing on developing next-generation artificial intelligence semiconductors that can process vast amounts of data while consuming energy efficiently. Neuromorphic computing, inspired by the human brain, is one of them. As a result, devices that mimic biological neurons and synapses are being developed one after another based on emerging materials and structures, but research on integrating individual devices into a system to verify and optimize them ...
The megalodon was less mega than previously believed
2024-01-22
A new study shows the Megalodon, a gigantic shark that went extinct 3.6 million years ago, was more slender than earlier studies suggested. This finding changes scientists’ understanding of Megalodon behavior, ancient ocean life, and why the sharks went extinct.
The Megalodon or megatooth shark is typically portrayed as a super-sized monster in popular culture, with recent examples in the sci-fi films “The Meg” (2018) and “Meg 2: The Trench” (2023). Previous studies assume that the shark likely reached lengths of at least 50 feet and possibly as much as 65 feet.
However, the Megalodon is largely known only from its teeth and vertebrae in the ...
Slender shark: Study finds Megalodon was not like a gigantic great white shark
2024-01-22
CHICAGO — A new scientific study shows that the prehistoric gigantic shark, Megalodon or megatooth shark, which lived roughly 15-3.6 million years ago nearly worldwide, was a more slender shark than previous studies have suggested.
Formally called Otodus megalodon, it is typically portrayed as a super-sized, monstrous shark in novels and sci-fi films, including “The Meg.” Previous studies suggest the shark likely reached lengths of at least 50 to 65 feet (15 to 20 meters). However, ...
New criteria for sepsis in children based on organ dysfunction
2024-01-21
Clinician-scientists from Ann & Robert H. Lurie Children’s Hospital of Chicago were among a diverse, international group of experts tasked by the Society of Critical Care Medicine (SCCM) with developing and validating new data-based criteria for sepsis in children. Sepsis is a major public heath burden, claiming the lives of over 3.3 million children worldwide every year. The new pediatric sepsis criteria – called the Phoenix criteria – follow the paradigm shift in the recent adult criteria that define sepsis as severe ...
Development and validation of the Phoenix criteria for pediatric sepsis and septic shock
2024-01-21
About The Study: In this international, multicenter, retrospective cohort study including more than 3.6 million pediatric encounters, a novel score, the Phoenix Sepsis Score, was derived and validated to predict mortality in children with suspected or confirmed infection. The new criteria for pediatric sepsis and septic shock based on the score performed better than existing organ dysfunction scores and the International Pediatric Sepsis Consensus Conference criteria.
Authors: Tellen D. Bennett, M.D., M.S., of the University of Colorado School of Medicine and Children’s Hospital Colorado in Aurora, is the corresponding author.
To access the ...
International consensus criteria for pediatric sepsis and septic shock
2024-01-21
About The Study: The Phoenix sepsis criteria for sepsis and septic shock in children were derived and validated by the international Society of Critical Care Medicine Pediatric Sepsis Definition Task Force using a large international database and survey, systematic review and meta-analysis, and modified Delphi consensus approach. A Phoenix Sepsis Score of at least 2 identified potentially life-threatening organ dysfunction in children younger than 18 years with infection, and its use has the potential to improve clinical care, epidemiological assessment, and research in pediatric sepsis and septic shock around the world.
Authors: R. Scott ...