(Press-News.org) PROVIDENCE, R.I. [Brown University] — To keep data safe in the cloud, a group of computer scientists suggests doing the Melbourne Shuffle.
That may sound like a dance move (and it is), but it's also a computer algorithm developed by researchers at Brown University.
The computing version of the Melbourne Shuffle aims to hide patterns that may emerge as users access data on cloud servers. Patterns of access could provide important information about a dataset — information that users don't necessarily want others to know — even if the data files themselves are encrypted.
"Encrypting data is an important security measure. However, privacy leaks can occur even when accessing encrypted data," said Olga Ohrimenko, lead author of a paper describing the algorithm. "The objective of our work is to provide a higher level of privacy guarantees, beyond what encryption alone can achieve."
The paper was presented this week at the International Colloquium on Automata, Languages, and Programming (ICALP 2014) in Copenhagen. Ohrimenko, who recently received her Ph.D. from Brown University and now works at Microsoft Research, co-authored the work with Roberto Tamassia and Eli Upfal, professors of computer science at Brown, and Michael Goodrich from the University of California–Irvine.
Cloud computing is increasing in popularity as more individuals use services like Google Drive and more companies outsource their data to companies like Amazon Web Services. As the amount of data on the cloud grows, so do concerns about keeping it secure. Most cloud service providers encrypt the data they store. Larger companies generally encrypt their own data before sending it to the cloud to protect it not only from hackers but also to keep cloud providers themselves from snooping around in it.
But while encryption renders data files unreadable, it can't hide patterns of data access. Those patterns can be a serious security issue. For example, a service provider — or someone eavesdropping on that provider — might be able to figure out that after accessing files at certain locations on the cloud server, a company tends to come out with a negative earnings report the following week. Eavesdroppers may have no idea what's in those particular files, but they know that it's correlated to negative earnings.
But that's not the only potential security issue.
"The pattern of accessing data could give away some information about what kind of computation we're performing or what kind of program we're running on the data," said Tamassia, chair of the Department of Computer Science.
Some programs have very particular ways in which they access data. By observing those patterns, someone might be able to deduce, for example, that a company seems to be running a program that processes bankruptcy proceedings.
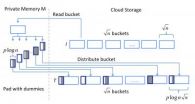
The Melbourne Shuffle aims to hide those patterns by shuffling the location of data on cloud servers. Ohrimenko named it after a dance that originated in Australia, where she did her undergraduate work.
"The contribution of our paper is specifically a novel data shuffling method that is provably secure and computationally more efficient than previous methods," Ohrimenko said.
It works by pulling small chunks of data down from the cloud and placing them in a user's local memory. Once the data is out of view of the server's prying eyes, it's rearranged — shuffled like a deck of cards — and then sent back to the cloud server. By doing this over and over with new blocks of data, the entirety of the data on the cloud is eventually shuffled.
The result is that data accessed in one spot today, may be in a different spot tomorrow. So even when a user accesses the same data over and over, that access pattern looks to the server or an eavesdropper to be essentially random.
"What we do is we obfuscate the access pattern," Tamassia said. "It becomes unfeasible for the cloud provider to figure out what the user is doing."
The researchers envision deploying their shuffle algorithm through a software application or a hardware device that users keep at their location. It could also be deployed in the form of a tamper-proof chip controlled by the user and installed at the data center of the cloud provider.
However it's deployed, the approach has the promise of lowering the cost of strong data security in an increasingly cloudy computer world.
INFORMATION: END
'Melbourne Shuffle' secures data in the cloud
2014-07-10
ELSE PRESS RELEASES FROM THIS DATE:
The bigger the better: Cigarette warning labels prompt quit attempts
2014-07-10
WASHINGTON - Cigarette warning labels can influence a smoker to try to quit even when the smoker is trying to avoid seeing the labels, according to a survey of thousands of adult smokers in four countries published by the American Psychological Association.
Small, text-only warning labels like those on cigarette packs in the United States prompt people to think about health risks of smoking, and people who notice the warnings regularly are more likely to try to quit, the research found. Larger, more graphic warning labels like those in other countries, such as Australia, ...
Radio-burst discovery deepens astrophysics mystery
2014-07-10
The discovery of a split-second burst of radio waves by scientists using the Arecibo radio telescope in Puerto Rico provides important new evidence of mysterious pulses that appear to come from deep in outer space.
The finding by an international team of astronomers, published July 10 in The Astrophysical Journal, marks the first time that a so-called "fast radio burst" has been detected using an instrument other than the Parkes radio telescope in Australia. Scientists using the Parkes Observatory have recorded a handful of such events, but the lack of any similar findings ...
Working to loosen the grip of severe mental illness
2014-07-10
A neuroscientist at Rutgers University-Newark says the human brain operates much the same whether active or at rest – a finding that could provide a better understanding of schizophrenia, bipolar disorder and other serious mental health conditions that afflict an estimated 13.6 million Americans.
In newly published research in the journal Neuron, Michael Cole, an assistant professor at the Center for Molecular and Behavioral Neuroscience, determined that the underlying brain architecture of a person at rest is basically the same as that of a person performing a variety ...
How antioxidants can accelerate cancers, and why they don't protect against them
2014-07-10
Cold Spring Harbor, NY – For decades, health-conscious people around the globe have taken antioxidant supplements and eaten foods rich in antioxidants, figuring this was one of the paths to good health and a long life.
Yet clinical trials of antioxidant supplements have repeatedly dashed the hopes of consumers who take them hoping to reduce their cancer risk. Virtually all such trials have failed to show any protective effect against cancer. In fact, in several trials antioxidant supplementation has been linked with increased rates of certain cancers. In one trial, ...
Depressed men with prostate cancer are diagnosed later stage, get less effective therapies
2014-07-10
Depressed men with localized prostate cancer were more likely to be diagnosed with more aggressive prostate cancer, received less effective treatments and survived for shorter times than prostate cancer patients who were not depressed, a UCLA study has found.
The negative outcomes may be the result of several factors such as bias against the mentally ill, depression's impact on biological cancer processes, the depressed man's lack of investment in his general health and disinterest in receiving more effective care, and missed opportunities by physicians to educate patients ...
Scientist finds link between antibiotics, bacterial biofilms and chronic infections
2014-07-10
Researchers from the University of Southern California and the Oak Crest Institute of Science have discovered the link between antibiotics and bacterial biofilm formation leading to chronic lung, sinus and ear infections. The study results, published in the current issue of PLOS ONE, illustrate how bacterial biofilms can actually thrive, rather than decrease, when given low doses of antibiotics.
"This research addresses the long standing issues surrounding chronic ear infections and why some children experience repeated ear infections even after antibiotic treatment," ...
BMSCs with Nogo-66 receptor gene silencing for repair of spinal cord injury
2014-07-10
After central nervous system injury, the increase in Nogo protein is mediated by Nogo-66 receptor gene, leading to the collapse of growth cones and inhibiting the extension of neuronal neurites. Zhiyuan Li and his team, Heibei Xingtai People's Hospital, China used RNA interference to silence Nogo-66 receptor gene expression in bone marrow mesenchymal stem cells (BMSCs), blocked the inhibitory effect of Nogo protein, promoted the process growth of neurons differentiated by transplanted cells, improved the therapeutic effects and increased the success rate of BMSCs transplantation ...
Inhibition of NgR expression reduces apoptotic retinal ganglion cells in diabetes
2014-07-10
Activation of Nogo receptor (NgR) is an essential factor of nerve regeneration inhibition, neuronal atrophy and even apoptosis. Upregulation of NgR expression is an important cause of cell apoptosis and visual extinction in some diseases including glaucoma. Whether ganglion cell apoptosis is related to NgR gene expression in diabetes mellitus remains poorly understood. Dr. Xuezheng Liu and his team, Liaoning Medical University, China interfered NgR expression in the retinal ganglion cells of rats with diabetes mellitus and found that Rho kinase expression was obviously ...
Fusion protein of single-chain variable domain fragments and myasthenia gravis
2014-07-10
Single-chain variable domain fragment (scFv) 637 is an antigen-specific scFv of myasthenia gravis and it can bind to acetylcholine receptor in the residues 67-76 of α-subunit of acetylcholine receptor. Dr. Fanping Meng and his team, College of Medicine, Yanbian University in China conjugated scFv and human serum albumin genes and detected the fusion protein in Pichia pastoris. Results showed that the fusion protein bound to acetylcholine receptors in neuromuscular junction of human intercostal muscle and the inhibition rate of fusion protein binding to acetycholine ...
How does miR-21 promote the differentiation of hair follicle-derived NCSCs into SCs?
2014-07-10
Hair follicle-derived neural crest stem cells (NCSCs) can be induced to differentiate into Schwann cells (SCs). However, the underlying regulatory mechanism during cell differentiation remains poorly understood. Dr. Yuxin Ni and her team, Hospital of Stomatology, Jilin University, China isolated NCSCs from human hair follicle and induced them to differentiate into SCs. MicroRNA (miR-21) expression was gradually increased during the differentiation of NCSCs into SCs. After transfection with the miR-21 agonist (agomir-21), the differentiation capacity of NCSCs was increased. ...