(Press-News.org) A widely used security protocol that dates back to the days of dial-up Internet has vulnerabilities that could expose large numbers of networked devices to an attack and allow an attacker to gain control of traffic on an organization's network.
A research team led by University of California San Diego computer scientists investigated the Remote Authentication Dial-In User Service (RADIUS) protocol and found a vulnerability they call Blast-RADIUS that has been present for decades. RADIUS, designed in 1991, allows networked devices such as routers, switches or mobile roaming gear to use a remote server to validate login or other credentials.
This is a common set-up in enterprise and telecommunications networks because it allows credentials to be centrally managed. As a result, RADIUS is a critical part of modern telecommunications and enterprise networks; in large enterprises, it may control access to tens of thousands of switches.
Authors of the paper “RADIUS/UDP Considered Harmful” include researchers from Cloudfare, Centrum Wiskunde & Informatica, BastiionZero and Microsoft Research. It was presented last week at the USENIX Security 2024 conference.
“This is among the largest and most complex vulnerability disclosure processes that we have been involved in, “ said Nadia Heninger, a professor in the Jacobs School of Engineering Department of Computer Science and Engineering. “Given how widely this protocol is used, it is surprising that it has received almost no formal security analysis in the academic cryptography and security communities.”
Heninger notes the large gap that existed between those who deploy these protocols and those who study them.
The researchers discovered the ability for a “man in the middle” to attack communication between a RADIUS client (or the victim’s networked device) and RADIUS server to forge a valid protocol accept message in response to a fake login or authentication request. This could give an attacker administrative access to networked devices and services without requiring an attacker to guess or “brute force” passwords.
The root of this vulnerability stems from the fact RADIUS was developed before proper cryptographic protocol design was well understood, the authors say. It uses an authentication check based on an ad hoc and insecure construction based on the MD5 hash function, which has been known to be broken for two decades.
However, the RADIUS protocol was not updated when MD5 was broken in 2004, the authors note. Before their work, the maintainers of the protocol standards defining RADIUS thought that the MD5-based construction used in RADIUS was still secure.
Vendors have released patches that implement the authors’ recommended short-term mitigation for this vulnerability. System administrators should check for patches for protocols they use with RADIUS and apply the updated configuration options suggested by their vendors.
The authors have disclosed their findings (security advisories CVE-2024-3596 and VU#456537) and more than 90 vendors have been involved in a coordinated disclosure and issued security bulletins.
The research team includes Heninger, Miro Haller and Adam Suhl of UC San DIego; Sharon Goldberg of Cloudfare; Mike Milano of BastionZero; Dan Shumow of Microsoft Research; and Marc Stevens of Centrum Wiskunde & Informatica.
END
Computer scientists discover vulnerabilities in a popular security protocol
2024-08-20
ELSE PRESS RELEASES FROM THIS DATE:
The emergence of moral foundations in children’s speech
2024-08-20
A study of children’s conversations with their caretakers sheds light on the timeline of the emergence of moral foundation words in the first six years of life in English-speaking children. Moral Foundations theory posits that morality is largely intuitive and underlaid by modular foundations. The original set of five foundations proposed by researchers includes Care/Harm, Fairness/Cheating, Authority/Subversion, Loyalty/Betrayal, and Purity/Degradation. Aida Ramezani and colleagues systematically ...
Correcting misperceptions of opposing party won’t reduce polarization
2024-08-20
Political animus between Republicans and Democrats in the United States is alarmingly high, raising fears of undemocratic or even violent actions. An often-touted intervention to prevent political polarization is to identify and correct misperceptions about people’s partisan opponents. Sean Westwood and colleagues sought to empirically test the effectiveness of this strategy. The authors surveyed 9,810 American partisans online from fall 2022 to fall 2023, finding that their opinions of whether ...
Scientists discover new code governing gene activity
2024-08-20
A newly discovered code within DNA – coined “spatial grammar” – holds a key to understanding how gene activity is encoded in the human genome.
This breakthrough finding, identified by researchers at Washington State University and the University of California, San Diego and published in Nature, revealed a long-postulated hidden spatial grammar embedded in DNA. The research could reshape scientists’ understanding of gene regulation and how genetic variations may influence gene expression in development or disease.
Transcription factors, the proteins that control which genes in one’s genome are turned on or off, ...
The invasion of Ukraine and European attitudes
2024-08-20
An ongoing survey captures how the Russian invasion of Ukraine affected attitudes in European countries not directly involved in the conflict. Margaryta Klymak and Tim Vlandas examine how the Russian invasion of Ukraine affected economic and political attitudes in eight European countries. The authors took advantage of the timing of the European Social Survey (ESS), which happened to be administered both just before and just after the Russian invasion of Ukraine in February 2022 in eight countries: Switzerland, Greece, Italy, Montenegro, Macedonia, Netherlands, Norway, and Portugal. Overall, the invasion increased support ...
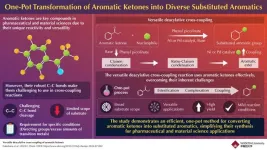
A new reaction to enhance aromatic ketone use in chemical synthesis
2024-08-20
Aromatic ketones have long been valuable intermediates in chemical synthesis, particularly in cross-coupling reactions where different chemical entities are combined to form new compounds. For instance, a process called deacylative cross-coupling removes the acyl group from the aromatic ketone, allowing it to bond with other chemicals and produce a wide variety of useful compounds. These reactions are crucial for producing a wide array of aromatic compounds used in various industries like agrochemicals.
However, the utility of aromatic ketones has been limited due to the difficulty in breaking their strong carbon-carbon bonds. These robust bonds are challenging to cleave, ...
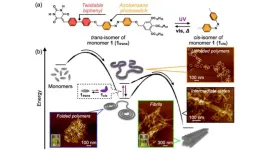
Investigating the interplay of folding and aggregation in supramolecular polymer systems
2024-08-20
In polymers, the competition between the folding and aggregation of chains, both at an individual level and between chains, can determine the mechanical, thermal, and conductive properties of such materials. Understanding the interplay of folding and aggregation presents a significant opportunity for the development and discovery of polymeric materials with tailored properties and functionalities.
This also holds true for non-covalent counterparts of conventional covalent polymers, i.e., supramolecular polymers (SPs). SPs are expected to have practical applications as novel stimuli-responsive ...
Adaptive 3D printing system to pick and place bugs and other organisms
2024-08-20
MINNEAPOLIS / ST. PAUL (08/20/2024) — A first-of-its-kind adaptive 3D printing system developed by University of Minnesota Twin Cities researchers can identify the positions of randomly distributed organisms and safely move them to specific locations for assembly. This autonomous technology will save researchers time and money in bioimaging, cybernetics, cryopreservation, and devices that integrate living organisms.
The research is published in Advanced Science, a peer-reviewed scientific journal. The researchers ...
Fossil hotspots in Africa obscure a more complete picture of human evolution
2024-08-20
WASHINGTON (August 20, 2024) – Much of the early human fossil record originates from just a few places in Africa, where favorable geological conditions have preserved a trove of fossils used by scientists to reconstruct the story of human evolution. One of these fossil hotspots is the eastern branch of the East African Rift System, home to important fossil sites such as Oldupai Gorge in Tanzania. Yet, the eastern branch of the rift system only accounts for 1% of the surface area of Africa—a fact that makes it possible to estimate how much information scientists who rely on such small samples are missing.
In ...
Extraterrestrial chemistry with earthbound possibilities
2024-08-20
DENVER, Aug. 20, 2024 — Who are we? Why are we here? As the Crosby, Stills, Nash & Young song suggests, we are stardust, the result of chemistry occurring throughout vast clouds of interstellar gas and dust. To better understand how that chemistry could create prebiotic molecules — the seeds of life on Earth and possibly elsewhere — researchers investigated the role of low-energy electrons created as cosmic radiation traverses through ice particles. Their findings may also inform medical and environmental applications on our home planet.
Undergraduate student Kennedy Barnes will present the team’s results at the fall meeting of the American ...
Deadly sea snail toxin could be key to making better medicines
2024-08-20
Scientists are finding clues for how to treat diabetes and hormone disorders in an unexpected place: a toxin from one of the most venomous animals on the planet.
A multinational research team led by University of Utah scientists has identified a component within the venom of a deadly marine cone snail, the geography cone, that mimics a human hormone called somatostatin, which regulates the levels of blood sugar and various hormones in the body. The hormone-like toxin’s specific, long-lasting effects, which help the snail hunt its prey, could also help scientists design better ...