(Press-News.org) The cybersecurity refrain when encountering phishing emails invariably advises: “don’t click on that link” and “report that email” — but new research from Drexel University and Arizona State University has revealed a problematic reality: Most major companies do little to support reporting and few take action to shut down phishing sites disguised as their own after they have been reported.
Recently presented at the International Symposium on Research in Attacks, Intrusions and Defense (RAID), an extensive investigation into reporting resources and processes — including an empirical test of their efficacy — revealed that less than half of Fortune 100 companies offer any channel for reporting these scams. And an experiment, to test the companies’ response to reports of phishing attacks impersonating their websites, found that nearly 30% of reported websites were never accessed as part of an investigation and only 3% of the were ever blocked from access.
Most phishing emails include links to download malware or visit fake webpages that mimic popular sites. Recipients may be tricked into attempting to log in to the sites, divulging their account information to the bad actors behind them. Variations on this cyberattack, called smishing, which involves sending malicious links in text messages; and vishing, which uses voicemails, are also becoming more prevalent.
Despite ever-evolving cybersecurity techniques to detect and block the malicious scams, many still make it through countermeasures and into inboxes. In 2022 the FBI received more reports of phishing than any other type of cybercrime — totaling an 11-fold increase since 2018.
Because of this evasiveness, most companies provide cybersecurity training to help employees identify and instruct them to report phishing emails as a last line of defense.
When phishing emails are reported, the companies that are being impersonated in them can take steps to mitigate the scam, including updating their security systems, re-securing compromised email accounts and reporting the fraud to federal authorities and report any website listed in the email so that it can be taken down, or “block listed.”
But research suggests that the rate of phishing attack reporting is strikingly low. A 2020 study by researchers at Arizona State showed that phishing sites are visited an average of 27 times before being reported.
In hopes of improving participation in anti-phishing measures, cybersecurity researchers from Drexel University’s College of Computing & Informatics sought to better understand the reporting ecosystem that has generated such a low rate of participation. Their report, which is one of the first comprehensive studies to look at the attitudes and actions around phishing reporting, uncovered the challenges and concerns people face when reporting, as well as shortcomings in how the reports are handled.
“Although users are constantly trained and instructed on how to identify and report phishing emails, the reaction they receive in the actions taken — or, more often, not taken — by the companies to which they report creates a negative feedback that discourages them from reporting future emails,” said Eric Sun, PhD, an assistant professor in Drexel’s College of Computing & Informatics who helped to lead the research. “Our research sheds a light on what it’s like to be a reporter and a company that receives a phishing report in hopes of improving this cybersecurity environment.”
The team approached its analysis from three perspectives, seeking to understand:
The options the cybersecurity ecosystem provides to individuals who wish to report phishing attacks
The actual experience in preparing to report a phishing attack
The post-reporting response — what happens to phishing websites after reporting and what feedback is conveyed to reporters
It found that although there is a great deal of room for improvement in the guidance information and feedback provided by companies and enforcement institutions, individual reporting of phishing attacks remains a crucial part of cybersecurity efforts.
What are the options for reporting?
After conducting an extensive search and filtering out official guidance offered by .gov, .org sites and the websites of the top 100 brand-name U.S. companies (Fortune 100), the team identified 575 webpages providing guidance about phishing attacks.
An analysis of those resources showed that there are five main channels for reporting phishing: email, built in reporting button in email software, SMS text, online reporting forms, and direct contact through a phone call or live chat.
The team identified eight government agencies and two anti-phishing organizations providing information and guidance about phishing: Federal Trade Commission (FTC), Internal Revenue Service (IRS), Cybersecurity & Infrastructure Security Agency (CISA), FBI Internet Crime Complaint Center (IC3), Department of Homeland Security (DHS), Department of Justice (DOJ), Federal Communications Commission (FCC), Government Information and Services, Anti-Phishing Working Group (APWG), and Phishing.org.
While all offered security advice on reporting phishing, only half of them actually provided dedicated channels for reporting phishing.
A summary of the advice offered by these agencies and organizations show that they primarily direct victims to one or several of 12 options: FTC, IRS, CISA, FCC, IC3, police, state attorney general’s office, APWG, the national SMS reporting number (7726), Google, the impersonated company, their internet service provider.
“Understandably, many organizations play a role in mitigating, investigating and enforcing laws against cybercrime, this can also raise confusion when it comes to reporting crimes like phishing,” said Gail-Joon Ahn, PhD, a professor at Arizona State University who helped to lead the research. “We found that due to this enforcement environment, a great deal of the reporting advice offered online is inconsistent or conflicting.”
The team’s analysis of reporting resources provided by Fortune 100 companies revealed that only 65 of them provide guidance to their customers on how to report a phishing attack. Only 44 of them provided channels for directly reporting a phishing attack impersonating — or “spoofing” — the company’s website, despite the prevalence of security advice recommending reporting such deceptions to those companies.
“We're constantly advised to avoid clicking on phishing links and to report them, especially to the spoofed companies,” Sun said. “Our finding that only 65 of the Fortune 100 companies provide advice for reporting phishing attacks — and less than half of them offer actual reporting channels — is particularly striking given these companies have more resources and are expected to be more committed to handling such reports.”
Through this analysis the group teased out four challenges common to both government/organizations and the Fortune 100 companies that may be discouraging people from reporting phishing attacks:
Reporting procedures for email phishing attacks typically do not require critical information, such as email headers (including sender and recipient details, timestamps, or IP addresses).
Different reporting channels offer different and sometimes conflicting or outdated advice. For example, some companies instruct victims to report the phishing, others just advise them to delete it without reporting.
Security advice requests people report the same phishing to too many places (i.e. FTC, IC3, and APWG).
Reporters generally do not receive feedback other than an auto-reply email confirming receipt of the report.
What’s it like to report a phishing attack?
In addition to understanding the existing reporting resources and guidance, the team tried to better understand the experience and sentiments of people who report phishing attacks.
To do it they recruited 89 U.S.-based participants to individually go through the process of locating reporting information and filing a report of a phishing attack. Surveying the participants after this short process provided a snapshot of peoples’ experience, attitudes and concerns about reporting.
Of the 89 participants, 15 decided not to report the phishing email. Most suggested it wasn’t worth the time they’d spend on it, or that nothing would be done with the report. Others noted that they would only file a report if it reached a certain threshold — receiving the same phishing email multiple times, for example.
Drops in reporting compliance were also observed when participants were advised to report the attack to multiple channels (e.g. the company and a government agency) — only half would follow the advice. Among participants with cybersecurity experience, only 39% indicated they would report it to multiple channels as requested. About half of the participants expressed a negative attitude about the reporting, including noting a lack of confidence that it would make a difference, or that they would receive a response.
“While it might not be all that surprising that there are some negative feelings about reporting, given the time commitment and perceived lack of results, we also discovered that about a third of respondents have limited knowledge about phishing reporting and a quarter were unaware that there were places to report phishing attacks,” said Adam Doupé, PhD, an associate professor at Arizona State, who helped to lead the research. “These are indicators that more could be done to educate the public about responding to phishing attacks.”
What happens after phishing is reported?
In the final step of their investigation the team looked at how companies and organizations responsible for dealing with phishing sites respond to reports. What they found indicates that concerns expressed by reporters about lack of response and communication are not unfounded.
The researchers used two observable actions as indicators of companies’ responsiveness to the reports: what happened to the reported phishing websites? And what feedback did the reporter receive?
They created a set of test phishing websites — in accordance with ethical research requirements and with prior notification of domain registrar and hosting service provider — spoofing the site of each Fortune 100 company. Over the course of two months, the team reported 14 times to each of the 39 companies that provided instructions for doing so. In addition, they reported all of the sites to the national SMS phishing reporting number (7726, the alphanumeric translation of “SPAM”).
During their experiments, the team found that reporting phishing attacks can be quite challenging. For instance, while some companies required them to forward phishing emails to a dedicated reporting address, the emails were often blocked due to the company’s own security measures. The filters flagged these emails as potentially harmful, stating, “A signature was detected that could either be a virus or a spam score over the maximum threshold,” thus preventing the reports from reaching the intended destination.
Following the reports, the researchers tracked how many of the sites were accessed — an indicator that the companies were investigating the report — and how many were ultimately blocked.
They found that 29 of the 39 companies accessed 184 of the reported sites, 10 companies did not access the sites at all. Only 3.3% of the sites reported via email to companies, per their instructions, were blocked. But the sites that were reported via 7726 were visited within seven hours of the report and more than 73% were blocked.
Of the 39 companies to which reports were filed, only 19 responded to the reporter and 15 of those responses were auto-replies. The reporter received no responses indicating a resolution — whether the phishing website had been taken down, for example.
“Our findings seem to confirm participants’ views that some companies may not care enough about the reports,” Ahn said. “In addition to the overall low response rate and lack of confirmation of a resolution, only four companies ever sent us a response indicating that the sites we had reported were indeed phishing sites.”
How can the vibe around phishing reporting be improved?
Taking their ample findings into consideration, the researchers suggest that to begin improving the phishing reporting ecosystems, companies and organizations responsible for addressing phishing attacks first need to become better communicators.
“Our research has identified a number of concerns from users, but the most significant is the outcome of reporting,” Sun said. “Many users are willing to report phishing attempts, but the lack of feedback is a key reason why they often don’t. Users are unsure if they are reporting through the correct channels and methods, whether their reports are being taken seriously, or if their actions are making a difference.”
Even automated responses would be an improvement, according to Sun, if they provide updates on actions being taken and the status of the reported site. Such correspondence would validate the reporters’ efforts and help to show that they are appreciated, which he suggests could encourage future reporting.
The next step the researchers recommended is providing clear and consistent security advice about how and where to report different types of phishing attacks. This would help to alleviate concerns about choosing the right reporting channel and reduce the effort and time involved in the process.
Sun notes that despite ongoing developments in cybersecurity technology, robust reporting, and a prompt response to block phishing sites, combined with detection technology, will continue to be the most reliable line of defense against these attacks.
“Phishing reporting is one of the few areas where end users — who bear the brunt of the harm in phishing attacks — can actively fight back and make a difference,” Sun said. “It is crucial to encourage people to report phishing attacks because technology alone will not stem the tide.”
END
Reporting into the void: Research validates victims' doubts about response to phishing reports
Empirical study suggests most Fortune 100 companies fall short when it comes to addressing phishing
2024-11-12
ELSE PRESS RELEASES FROM THIS DATE:
Decoding Deception: The Psychology of Combating Misinformation
2024-11-12
Decoding Deception: The Psychology of Combating Misinformation, a short film produced by Proceedings of the National Academy of Sciences with support from the Pulitzer Center, addresses one of the most pressing issues of our time: the quest to stem the swelling tide of misinformation.
Decoding Deception explores potential remedies to this growing societal problem. While social media acts as an accelerant for the rampant spread of misinformation on climate change, public health, and politics, the rise of generative AI risks worsening the problem. Left unchecked, disinformation and misinformation can inflict lasting damage on people, institutions, and society ...
Plant green-up and herbivory in Greenland
2024-11-12
A study links herbivory to phenology in the Arctic. Phenology is the study of the timing of events in the natural world. In recent decades, researchers have investigated how climate change is shifting many natural events. Eric Post and colleagues wanted to understand how a different variable—the presence or absence of herbivores—affects the timing of spring plant growth, or green-up, in Greenland. In an experiment lasting nine years, the authors excluded musk oxen and caribou from some areas, then compared the timing of the spring green-up of 9 tundra plant species in the areas with and without herbivores. Of the plants that showed altered green-up between the conditions, about ...
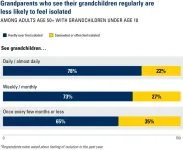
Grandparents help grandkids in many ways – but the reverse may be true too, poll suggests
2024-11-12
As many Americans prepare to gather with their families for the holidays, a new poll shows the importance of grandchildren in grandparents’ lives.
The poll also suggests that having grandchildren and seeing them regularly may have a link to older adults’ mental health and risk of loneliness.
Although the poll can’t show cause and effect, the findings suggest a need to study the role of grandparenting in older adults’ lives, as part of a broader effort to address social isolation.
At ...
Giving robots superhuman vision using radio signals
2024-11-12
In the race to develop robust perception systems for robots, one persistent challenge has been operating in bad weather and harsh conditions. For example, traditional, light-based vision sensors such as cameras or LiDAR (Light Detection And Ranging) fail in heavy smoke and fog.
However, nature has shown that vision doesn't have to be constrained by light’s limitations — many organisms have evolved ways to perceive their environment without relying on light. Bats navigate using the echoes of sound waves, while sharks hunt by sensing electrical fields from their prey's movements.
Radio waves, whose wavelengths are orders of magnitude ...
Digital twins and complexity data science
2024-11-12
A Perspective suggests that “digital twins” are not simply tools for science but are an example of the integration of complexity science and data science into a new scientific field. A “digital twin” is a digital representation of a real-world object or system. The idea emerged from manufacturing but has been adopted by science, especially by the fields of medicine, immunology, and epidemiology. Digital twins are typically frequently or continuously updated and improved with real data from the real object the digital twin mirrors, allowing ...
‘Moonlighting’ enzymes can lead to new cancer therapies
2024-11-12
Researchers at the Centre for Genomic Regulation (CRG) reveal that metabolic enzymes known for their roles in energy production and nucleotide synthesis are taking on unexpected "second jobs" within the nucleus, orchestrating critical functions like cell division and DNA repair.
The discovery, reported across two separate research papers out today in Nature Communications, not only challenges longstanding biological paradigms in cellular biology but also opens new avenues for cancer therapies, particularly against aggressive tumours like triple-negative breast cancer (TNBC).
For decades, biology textbooks have neatly compartmentalised ...
One genomic test can diagnose nearly any infection
2024-11-12
Next-generation metagenomic sequencing test developed at UCSF proves its effectiveness in quickly diagnosing almost any kind of pathogen.
A genomic test developed at UC San Francisco to rapidly detect almost any kind of pathogen – virus, bacteria, fungus or parasite – has proved successful after a decade of use.
The test has the potential to vastly improve care for neurological infections that cause diseases like meningitis and encephalitis, as well as speed up the detection of new viral pandemic threats. It uses a powerful genomic sequencing ...
Blood vessel-like coating could make medical devices safer for patients
2024-11-12
University of B.C. researchers have developed a groundbreaking coating that could make medical devices safer for millions of patients, reducing the risks associated with blood clots and dangerous bleeding.
The new material, designed to mimic the natural behavior of blood vessels, could allow for safer use of blood-contacting devices like catheters, stents, blood-oxygenation machines and dialysis machines—especially in cases where blood clots are a significant concern.
“This discovery could be a transformative step in the development of safer medical devices,” said Dr. Jayachandran Kizhakkedathu, ...
Sleep is no light matter for bees
2024-11-12
In an emerging red flag for the digital era, sleep experts have warned us to avoid screen time in bed, sounding the alarm that light emitted from phones and other electronic devices can disrupt our sleep patterns. That’s one way that science is waking up to the broad range of health and disease implications related to circadian biology and our daily sleep-wake cycles.
Now, researchers at the University of California San Diego have found that light disruption is not only a health concern for humans. A new study led by PhD candidate Ashley Kim and Professor James Nieh in the School of Biological Sciences has found that artificial light disrupts the circadian rhythms of ...
New study explores the role of BMI in disease risk
2024-11-12
New study from deCODE genetics/Amgen highlights the importance of BMI in pathogenesis of disease, suggesting that reducing BMI alone could lower the risk of several diseases.
Scientists at deCODE genetics, subsidiary of Amgen, published a study today in Nature Communications that sheds light on how Body Mass Index (BMI) influences the risk of various diseases that are comorbid with obesity. The study, which used genetic data from Iceland and the UK Biobank, looked at whether disease risk associated with BMI-related sequence variants are explained completely or partially by their effect on BMI.
The results showed that for some conditions, such as fatty liver disease, glucose intolerance, ...
LAST 30 PRESS RELEASES:
Alkali cation effects in electrochemical carbon dioxide reduction
Test platforms for charging wireless cars now fit on a bench
$3 million NIH grant funds national study of Medicare Advantage’s benefit expansion into social supports
Amplified Sciences achieves CAP accreditation for cutting-edge diagnostic lab
Fred Hutch announces 12 recipients of the annual Harold M. Weintraub Graduate Student Award
Native forest litter helps rebuild soil life in post-mining landscapes
Mountain soils in arid regions may emit more greenhouse gas as climate shifts, new study finds
Pairing biochar with other soil amendments could unlock stronger gains in soil health
Why do we get a skip in our step when we’re happy? Thank dopamine
UC Irvine scientists uncover cellular mechanism behind muscle repair
Platform to map living brain noninvasively takes next big step
Stress-testing the Cascadia Subduction Zone reveals variability that could impact how earthquakes spread
We may be underestimating the true carbon cost of northern wildfires
Blood test predicts which bladder cancer patients may safely skip surgery
Kennesaw State's Vijay Anand honored as National Academy of Inventors Senior Member
Recovery from whaling reveals the role of age in Humpback reproduction
Can the canny tick help prevent disease like MS and cancer?
Newcomer children show lower rates of emergency department use for non‑urgent conditions, study finds
Cognitive and neuropsychiatric function in former American football players
From trash to climate tech: rubber gloves find new life as carbon capturers materials
A step towards needed treatments for hantaviruses in new molecular map
Boys are more motivated, while girls are more compassionate?
Study identifies opposing roles for IL6 and IL6R in long-term mortality
AI accurately spots medical disorder from privacy-conscious hand images
Transient Pauli blocking for broadband ultrafast optical switching
Political polarization can spur CO2 emissions, stymie climate action
Researchers develop new strategy for improving inverted perovskite solar cells
Yes! The role of YAP and CTGF as potential therapeutic targets for preventing severe liver disease
Pancreatic cancer may begin hiding from the immune system earlier than we thought
Robotic wing inspired by nature delivers leap in underwater stability
[Press-News.org] Reporting into the void: Research validates victims' doubts about response to phishing reportsEmpirical study suggests most Fortune 100 companies fall short when it comes to addressing phishing