(Press-News.org) A computer science engineer at Michigan State University has a word of advice for the millions of bitcoin owners who use smartphone apps to manage their cryptocurrency: don't. Or at least, be careful. Researchers from MSU are developing a mobile app to act as a safeguard for popular but vulnerable "wallet" applications used to manage cryptocurrency.
"More and more people are using bitcoin wallet apps on their smartphones," said Guan-Hua Tu, an assistant professor in MSU's College of Engineering who works in the Department of Computer Science and Engineering. "But these applications have vulnerabilities."
Smartphone wallet apps make it easy to buy and trade cryptocurrency, a relatively new digital currency that can be challenging to understand in just about every way except one: It's very clearly valuable. Bitcoin was the most valuable cryptocurrency at the time of writing, with one bitcoin being worth more than $55,000.
But Tu and his team are uncovering vulnerabilities that can put a user's money and personal information at risk. The good news is that the team is also helping users better protect themselves by raising awareness about these security issues and developing an app that addresses those vulnerabilities.
The researchers showcased that app -- the Bitcoin Security Rectifier -- in a paper published for the Association for Computing Machinery's Conference on Data and Application Security and Privacy. In terms of raising awareness, Tu wants to help wallet users understand that these apps can leave them vulnerable by violating one of Bitcoin's central principles, something called decentralization.
Bitcoin is a currency that's not tied to any central bank or government. There's also no central computer server that stores all the information about bitcoin accounts, such as who owns how much.
"There are some apps that violate this decentralized principle," Tu said. "The apps are developed by third parties. And, they can let their wallet app connect with their proprietary server that then connects to Bitcoin."
In essence, Bitcoin Security Rectifier can introduce a middleman that Bitcoin omits by design. Users often don't know this and app developers aren't necessarily forthcoming with the information.
"More than 90% of users are unaware of whether their wallet is violating this decentralized design principle based on the results of a user study," Tu said. And if an app violates this principle, it can be a huge security risk for the user. For example, it can open the door for an unscrupulous app developer to simply take a user's bitcoin.
Tu said that the best way users can safeguard themselves is to not use a smartphone wallet app developed by untrusted developers. He instead encourages users to manage their bitcoin using a computer -- not a smartphone -- and resources found on Bitcoin's official website, bitcoin.org. For example, the site can help users make informed decisions about wallet apps.
But even wallets developed by reputable sources may not be completely safe, which is where the new app comes in.
Most smartphone programs are written in a programming language called Java. Bitcoin wallet apps make use of a Java code library known bitcoinj, pronounced "bitcoin jay." The library itself has vulnerabilities that cybercriminals could attack, as the team demonstrated in its recent paper.
These attacks can have a variety of consequences, including compromising a user's personal information. For example, they can help an attacker deduce all the Bitcoin addresses that wallet users have used to send or receive bitcoin. Attacks can also send loads of unwanted data to a user, draining batteries and potentially resulting in hefty phone bills.
Tu's app is designed to run at the same time on the same phone as a wallet, where it monitors for signs of such intrusions. The app alerts users when an attack is happening and provides remedies based on the type of attack, Tu said. For example, the app can add "noise" to outgoing Bitcoin messages to prevent a thief from getting accurate information.
"The goal is that you'll be able to download our tool and be free from these attacks," Tu said.
The team is currently developing the app for Android phones and plans to have it available for download in the Google Play app store in the coming months. There's currently no timetable for an iPhone app because of the additional challenges and restrictions posed by iOS, Tu said.
In the meantime, though, Tu emphasized that the best way users can protect themselves from the insecurities of a smartphone bitcoin wallet is simply by not using one, unless the developer is trusted.
"The main thing that I want to share is that if you do not know your smartphone wallet applications well, it is better not to use them since any developer -- malicious or benign -- can upload their wallet apps to Google Play or Apple App Store," he said.
INFORMATION:
Also collaborating on this project were MSU's Professor Li Xiao as well as Ph.D. students Yiwen Hu and Sihan Wang, all from the Department of Computer Science and Engineering. This work was funded in part by the National Science Foundation.
A new USC study suggests that certain neighborhoods - particularly those characterized by poverty and unemployment - may pose an environmental risk to the developing brains of children, impacting neurocognitive performance and even brain size.
The research was published May 3 in the journal JAMA Pediatrics.
These findings highlight the importance of neighborhood environments for child and adolescent brain development, the researchers said, and suggest that policies, programs and investments that help improve local neighborhood conditions and empower communities could support children's neurodevelopment and long-term health.
"This is the first large, national study ...
Using a bit of machine learning magic, astrophysicists can now simulate vast, complex universes in a thousandth of the time it takes with conventional methods. The new approach will help usher in a new era in high-resolution cosmological simulations, its creators report in a study END ...
Many miles of streams and rivers in the United States and elsewhere are polluted by toxic metals in acidic runoff draining from abandoned mining sites, and major investments have been made to clean up acid mine drainage at some sites. A new study based on long-term monitoring data from four sites in the western United States shows that cleanup efforts can allow affected streams to recover to near natural conditions within 10 to 15 years after the start of abatement work.
The four mining-impacted watersheds--located in mountain mining regions of California, Colorado, Idaho, and Montana--were all designated as Superfund sites under the Comprehensive Environmental Response, Compensation, and Liability Act (CERCLA), which helps ...
A universe evolves over billions upon billions of years, but researchers have developed a way to create a complex simulated universe in less than a day. The technique, published in this week's Proceedings of the National Academy of Sciences, brings together machine learning, high-performance computing and astrophysics and will help to usher in a new era of high-resolution cosmology simulations.
Cosmological simulations are an essential part of teasing out the many mysteries of the universe, including those of dark matter and dark energy. But until now, researchers faced the common conundrum of not being ...
As pandemic lockdowns went into effect in March 2020 and millions of Americans began working from home rather than commuting to offices, heavy traffic in America's most congested urban centers--like Boston--suddenly ceased to exist. Soon afterwards, the air was noticeably cleaner. But that wasn't the only effect. A team of Boston University biologists who study how human-related sounds impact natural environments seized the opportunity to learn how the reduced movement of people would impact local ecosystems. They found--surprisingly--that sound levels increased in some nature conservation areas, a result of cars driving faster on roads no longer choked by traffic.
BU ecologist Richard Primack and Carina Terry, an undergraduate student working in Primack's ...
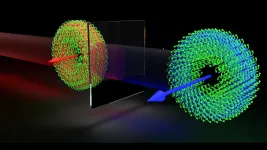
Spinning or rotating objects are commonplace, from toy tops, fidget spinners, and figure skaters to water circling a drain, tornadoes, and hurricanes.
In physics, there are two kinds of rotational motion: spin and orbital. Earth's motion in our solar system illustrates these; the daily 360-degree rotation of Earth around its own axis is spin rotation, while Earth's yearly trip around the sun is orbital rotation.
The quantity in physics defined to describe such motion is angular momentum (AM). AM is a conserved quantity: given an initial amount of it, it can be broken up and redistributed among particles such as atoms and photons, ...
BOSTON -- Immunity often calls to mind the adaptive immune response, made up of antibodies and T cells that learn to fight specific pathogens after infection or vaccination. But the immune system also has an innate immune response, which uses a set number of techniques to provide a swift, non-specialized response against pathogens or support the adaptive immune response.
In the past few years, however, scientists have found that certain parts of the innate immune response can, in some instances, also be trained in response to infectious pathogens, such as HIV. Xu Yu, MD, a Core Member of the Ragon Institute of MGH, MIT and Harvard, and colleagues ...
Adults are more compassionate and are up to twice as likely to donate to charity when children are present, according to a new study from psychologists.
The research, conducted by social psychologists at the University of Bath and Cardiff University and funded by the Economic and Social Research Council (ESRC), examined how the presence of children influences adults' compassionate motivations and behaviours.
Across eight experiments and more than 2,000 participants, the researchers asked adults to describe what typical children are like. After focusing on children in this way, participants ...
A hot topic symposia session during the Pediatric Academic Societies (PAS) 2021 Virtual Meeting will discuss a multipronged approach to addressing childhood adversity and promoting resilience - at the clinical, systems, community and educational levels.
The effect of adverse childhood experiences (ACEs) on health outcomes across the lifespan is well recognized among pediatric practitioners. Increasing the ability of healthcare providers to recognize and respond to ACEs can buffer the long-term negative physical and mental health impacts of adversity and increase patient-centered care.
"In the era of COVID-19, ...
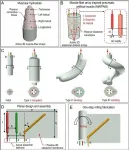
Biological organisms (such as elephant trunks, octopus tentacles, and human tongues) show remarkable dexterity and self-adaptation in unstructured environments, relying on the multiple-mode actuations of the skeleton-free muscular hydrostats. In general, muscular hydrostats mainly consist of well-ranged active 3D muscle-fiber arrays bundled by passive connective tissues (Fig. 1A). By selectively actuating the active 3D muscle-fiber arrays, muscular hydrostats can generate elongation, bending, contraction and twisting. Producing such multiple-mode actuation of muscular hydrostats is an interesting but long-lasting challenge in the field of robotics.
During past decades, many artificial muscles (such ...