Determining maximum allowable current of an RBS using a directed graph model and greedy algorithm
2024-07-26
(Press-News.org)
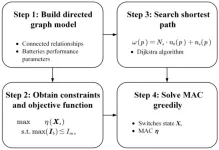
The central principle of the proposed MAC determination method is to connect the batteries within an RBS in parallel to the maximum possible extent, thereby maximizing the output current. To achieve this universally and automatically, the overall process is divided into the 4 steps shown in Fig. 1. First, a directed graph model is established for the subsequent computations. The nodes in the directed graph correspond to the connection points of components in the actual RBS. The edges in the directed graph correspond to the batteries, switches, and external electrical loads in the actual RBS. Each edge is assigned 2 attributes, a voltage difference and a resistance, based on the equivalent method. The model not only contains the connected relationships between batteries and switches but also retains the performance parameters of the batteries. Second, based on the equivalent circuit model, the MAC calculation problem is transformed into specific objective functions and constraints. The topology in the directed graph model is represented in the form of a matrix A in which element akl equals 1 for edge l leaving node k, -1 for edge l entering node k, or 0 otherwise. The dimensions of matrix A are reduced according to specific regulations of akl. Matrix Xs determines whether switch Sj is closed. According to Kirchhoff ’s laws, the output current Io and the currents of each battery Ib are ultimately represented, and the equivalent admittance matrix Yn of the circuit is defined. The indicator η is defined by the ratio of Io to max(Ib). To this end, the problem of finding the MAC is formulated as: max η(Xs), s.t. max(Ib)≤Im. Third, the shortest paths (SPs) (where additional batteries and switches on the path are penalized for distance) of the batteries are obtained using the Dijkstra algorithm to connect the batteries in the RBS in parallel. The distance ω of path p is ω(p) = Nsnb(p) + ns(p) and the shortest path SPi for battery Bi is SPi = arg min ω(p). Fourth, a greedy algorithm is used to organize the switches, allowing the batteries to connect via their SPs while satisfying the constraints, resulting in the MAC of the RBS.
Fig. 1. A diagram of the proposed method, which contains 4 main steps.
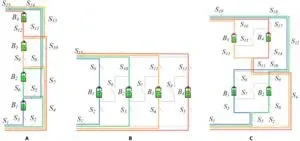
Then, the proposed method is applied to determine the MACs of 2 published RBS structures and a new one with a more complex structure, as shown in Fig. 5 (a) to (c) respectively. The following RBS systems are investigated and compared. (a) 3 different structures with the same 4 batteries. After obtaining the SPs, the MACs of the 3 RBS structures with 4 batteries are calculated using the proposed greedy algorithm. To verify and compare the proposed greedy algorithm, we also used the brute-force algorithm, which iterates through all possible switch states, and the heuristic algorithms (SA and GA) to calculate the MACs of the same RBSs. The final results of the brute-force algorithm are the same as those of the greedy algorithm. (b) the same structure as in Fig. 5C with 2/4/6 batteries. In this case, the proposed greedy algorithm still converges the fastest and achieves the correct MAC. The SA algorithm fails to obtain the correct MAC within the given number of iteration steps in the case of the 6-battery RBS structure. (c) the 4-battery structure in Fig. 5C with random isolated batteries. There are 4 possible scenarios for isolated batteries: (1) a single unhealthy battery, (2) 2 unhealthy batteries located in different substructures, (3) 2 unhealthy batteries located in the same substructure, and (4) 3 unhealthy batteries. The resulting MAC (η) values for these 4 scenarios are 2, 2, 1, and 1, respectively.
Fig. 5. Calculation results about the SPs in different 4-battery RBS structures.
Finally, the calculation results, computational complexity of the algorithm, and scenarios such as battery random isolation are also discussed sequentially. The correctness of the outcomes provided by the proposed greedy algorithm will now be discussed from 2 perspectives: circuit analysis and validation against the brute-force algorithm. On the one hand, adding more batteries to the main circuit only creates a series structure and does not improve the MAC, thus the switch-control scheme provided by the proposed greedy algorithm maximizes the RBS output current. On the other hand, the brute-force method yields the same η, indicating that the proposed greedy algorithm successfully identifies the MAC among all the potential reconfigured structures. The proposed greedy algorithm possesses a significant advantage in terms of its effectiveness and efficiency. As depicted in Fig. 7A to C, the brute-force algorithm comes at a high computational cost while ensuring the correctness of the results by exploring all possible switch states. The SA and GA algorithms require more iterations to converge to the final solution than the proposed greedy algorithm. Furthermore, this approach can handle RBSs with arbitrary structures, which is another significant advantage. Most of the existing RBS structures have simple topological characteristics, so calculating their MACs is relatively straightforward or even intuitive. However, these simple structures do not always fully satisfy the requirements of complex applications, such as dynamically adapting the circuit to variable and random operating conditions or actively equalizing differences between batteries in the RBS. Moreover, isolating the batteries disrupts the original regularity and symmetry of the topology, which complicates the otherwise simple structure, and the maximum output current of the system becomes more challenging to obtain. In contrast, the proposed method calculates the MAC of arbitrary RBS structures, most notably complex and flexible RBS structures.
Fig. 7. Temporal evolution of objective values in the iteration process for calculating RBS structures. (A) Evolution for the structure shown in Fig. 5A. (B) Evolution for the structure shown in Fig. 5B. (C) Evolution for the structure shown in Fig. 5C.
END
ELSE PRESS RELEASES FROM THIS DATE:
2024-07-26
Highlights
-Developed a 21-language, fast and high-fidelity neural text-to-speech technology
-The developed model can synthesize one second of speech at high speed in only 0.1 seconds using a single CPU core, which is about eight times faster than the conventional methods
-The developed model can realize fast synthesis with a latency of 0.5 seconds on a smartphone without network connection
-The technology is expected to be introduced into speech applications, such as multilingual speech translation and car navigation
Abstract
The Universal Communication Research Institute of the National Institute of Information and Communications Technology (NICT, President: TOKUDA Hideyuki, ...
2024-07-26
East Hanover, NJ – July 26, 2024 – Children with special health care needs (CSHCN) often face significant disruptions in their education due to extended hospitalizations. A recent study published online in Disability and Rehabilitation on July 1, 2024, by a multidisciplinary team of Kessler Foundation and Children Specialized Hospital researchers, highlights critical areas needing attention to ensure smoother school re-entries for CSHCN, ensuring they receive the necessary educational support post-hospitalization.
Involving parents, former patients, and rehabilitation ...
2024-07-26
Doctors and others who take care of hospitalized patients may want to sit down for this piece of news.
A new study suggests that getting at a patient’s eye level when talking with them about their diagnosis or care can really make a difference. Sitting or crouching at a hospitalized patient’s bedside was associated with more trust, satisfaction and even better clinical outcomes than standing, according to the new review of evidence.
The study’s authors, from the University of Michigan and VA Ann Arbor Healthcare System, note that most of the studies on this topic varied with their interventions and outcomes, and were found to have high risk of bias. Their ...
2024-07-26
More and more studies show that men face risks of cancer from BRCA1 and BRCA2 genetic mutations that are most often associated with breast and ovarian cancers in women.
According to a July 25 JAMA Oncology review article by experts at Fred Hutch Cancer Center and University of Washington, newly developed national screening guidelines offer hope for identifying the cancer risk of BRCA mutations in men through genetic testing and tailored cancer screening.
“Not enough men are getting genetic testing to see if they carry a BRCA1 or BRCA2 gene ...
2024-07-26
MINNEAPOLIS / ST. PAUL (07/25/2024) — Engineering researchers at the University of Minnesota Twin Cities have demonstrated a state-of-the-art hardware device that could reduce energy consumption for artificial intelligent (AI) computing applications by a factor of at least 1,000.
The research is published in npj Unconventional Computing, a peer-reviewed scientific journal published by Nature. The researchers have multiple patents on the technology used in the device.
With the growing demand of AI applications, researchers have been looking ...
2024-07-26
Houston, Texas, July 26, 2024 – The Texas Heart Institute (THI), a globally renowned cardiovascular health center, and BiVACOR®, a leading clinical-stage medical device company, are pleased to provide an update on the condition of the first patient to receive the BiVACOR Total Artificial Heart (TAH) implant on July 9, as part of the U.S. Food and Drug Administration (FDA) Early Feasibility Study (EFS). On July 17, eight days following the BiVACOR TAH implant, a donor heart became available and was transplanted into the ...
2024-07-26
The color palette of the birds you see out your window depend on where you live. If you’re far from the Equator, most birds tend to have drab colors, but the closer you are to the tropics, you’ll probably see more and more colorful feathers. Scientists have long been puzzled about why there are more brilliantly-colored birds in the tropics than in other places, and they’ve also wondered how those brightly-colored birds got there in the first place: that is, if those colorful feathers evolved in the tropics, or if tropical birds have colorful ancestors that came to the region from somewhere else. In a new study published ...
2024-07-26
Tokyo, Japan – Ice is far more complicated than most of us realize, with over 20 different varieties known to science, forming under various combinations of pressure and temperature. The kind we use to chill our drinks is known as ice I, and it’s one of the few forms of ice that exist naturally on Earth. Researchers from Japan have recently discovered another type of ice: ice 0, an unusual form of ice that can seed the formation of ice crystals in supercooled water.
The formation of ice near the surface ...
2024-07-26
Lack of persistence of CAR T cells is major limiting step in CAR T-cell therapy
Made by fusing an immune-stimulatory molecule to a protein from cancer cells, the therapy selectively targets CAR T cells and enhances their functionality and persistence in the body, extending their attack on cancer.
The therapy, called CAR-Enhancer (CAR-E), also causes CAR T cells to retain a memory of the cancer, allowing them to mount another attack if cancer recurs
BOSTON – Even as they have revolutionized the treatment of certain forms of cancer, CAR T-cell therapies ...
2024-07-26
EVANSTON, Ill. --- One of just two vertebrates without a jaw, sea lampreys that are wreaking havoc in Midwestern fisheries are simultaneously helping scientists understand the origins of two important stem cells that drove the evolution of vertebrates.
Northwestern University biologists have pinpointed when the gene network that regulates these stem cells may have evolved and gained insights into what might be responsible for lampreys’ missing mandibles.
The two cell types — pluripotent blastula cells (or embryonic stem cells) and neural crest cells — are both “pluripotent,” ...
LAST 30 PRESS RELEASES:
[Press-News.org] Determining maximum allowable current of an RBS using a directed graph model and greedy algorithm